
Introduction:
Imagine your entire CI/CD pipeline exposed, with sensitive data and code vulnerable to theft. That’s the chilling reality facing millions of organizations thanks to a critical vulnerability in Jenkins, affecting 43% of cloud environments. This vulnerability, CVE-2024-23897, allows attackers to potentially steal data, disrupt pipelines, or even launch ransomware attacks.
Don’t panic, but act fast! This post will equip you with the knowledge and steps to protect your Jenkins server and mitigate this critical risk.
The Threat:
Lurking within Jenkins’ core Java code lies a vulnerability in the Groovy Expression Language (SpEL) engine. A malicious attacker could exploit this vulnerability by crafting a specially crafted SpEL expression, granting them unauthorized access to your server. The consequences are dire:
- Data Breaches: Attackers could steal source code, user credentials, or customer information.
- Pipeline Disruption: Malicious manipulation could lead to delays, errors, and broken deployments.
- Ransomware Attacks: Your critical data could be encrypted, demanding ransom for its release.
The Good News:
There’s a patch! The Jenkins project released version 2.392 on January 24th, 2024, specifically addressing this vulnerability. Update your Jenkins server immediately to this version or later.
Protect Yourself:
Beyond patching, here are crucial steps to fortify your defenses:
- Scan your environment: Use a vulnerability scanner to identify any unpatched Jenkins instances. Patch them immediately!
- Security Best Practices: Implement strong passwords, multi-factor authentication, access restrictions, and regular monitoring.
- Stay Informed: Subscribe to Jenkins security advisories and relevant sources for timely updates.

How to remediate the Jenkins vulnerability
Due to the critical nature of this vulnerability, it is highly recommended to update the Jenkins server as soon as possible to Jenkins 2.442, LTS 2.426.3. If upgrading is not possible immediately, the Jenkins team recommends disabling access to the CLI. This should prevent any exploitation of the vulnerability and not require a restart of the server.
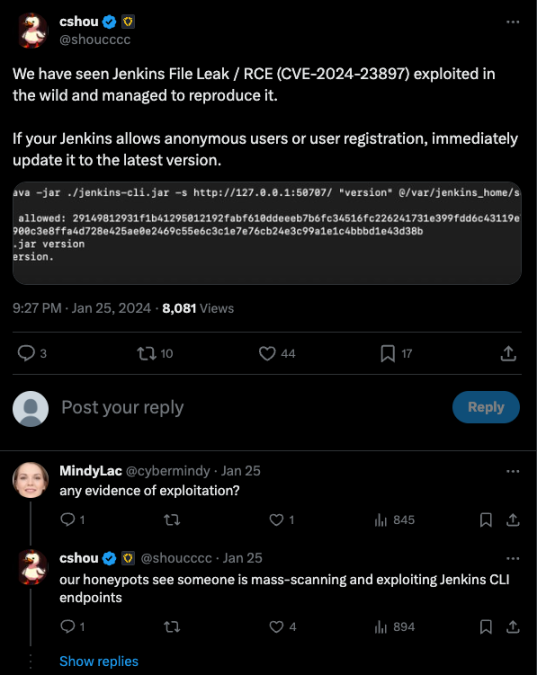
How can hackers abuse the vulnerability?
This flaw in handling the ‘@’ character allows attackers to view sensitive files in the Jenkins instance such as etc/passwd, etc/shadow, keys files, source code and more.
In addition to that, this vulnerability allows remote code execution in several scenarios presented in Jenkins’ advisory. For example a stored XSS through build logs, a “Remember Me” cookie and CSRF protection bypass. Jenkins noted that this attack scenario list is not final, and it is likely that there are more scenarios that could lead to RCE by exploiting this vulnerability.
The vulnerability has several POCs available online, and many organizations have already reported exploitation attempts towards publicly facing instances.
Conclusion:
Cybersecurity is an ongoing battle, but with vigilance and proactive measures, you can significantly reduce your risk. Patch your Jenkins server, implement best practices, and stay informed. Remember, early detection and remediation are key to safeguarding your organization.